TURN
Updated 29 April 2020

Introduction
TURN (Traversal Using Relay NAT) is a protocol for a node to receive incoming data behind a NAT or a firewall via TCP or UDP connections. This is particularly useful for nodes behind symmetric NATs, or else for firewalls that must receive incoming data when connecting to a specific node, or peer.
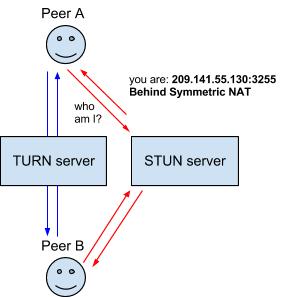
A TURN server is an advanced STUN server, which means any TURN can also act as a STUN. STUN (Session Traversal Utilities for NAT) is a network protocol designed to allow the client behind a NAT or several NAT servers to define its external IP address, the way the address and the port names will be communicated in the external network depending on the internal port number. This parameters are used for establishing a UDP connection between two hosts that are both behind a NAT router.
A TURN server is used as a relay if direct connection is impossible, thus transforming a p2p connection into a server-client one. WebRTC is a solution. It uses the ICE protocol - which, in its turn, needs additional servers (such a STUN or a TURN). WebRTC is a Web browser technology for connecting two clients for audio and video transmission. Its main features are integrated support by Web browsers and connecting clients as peer-to-peer (p2p) hosts, with no additional servers needed.
Establishing a p2p connection is not a trivial task, as all computers do not have public IPs. The NAT (Network Address Translation) technology was developed to create private networks used by individuals, to avoid running out of IPv4 addresses, and also for security reasons. Many home routers nowadays support the NAT technology, thus allowing all home devices to go online, even though Internet providers usually assign one IP address to one home network. All public IP addresses are unique, while the private ones are not. This is why p2p connections are not an easy task.
LXC configuration
We suggest that you install your TURN server in a dedicated container, first setting it up according to the manual.
TURN server installation
Install the coturn server for TURN
emerge -a net-im/coturn
Getting Let's Encrypt certificate
Get the domain certificate for turn.example.org, as explained in the manual.
TURN server configuration
Copy the default settings:
cp /etc/turnserver.conf.default /etc/turnserver.conf
Create a secret key:
openssl rand -hex 16
4b85833c7fdf06130bd7398ac9af558b
Now configure your TURN server: 443 will be its SSL port, 1.2.3.4 its external IP, 4b85833c7fdf06130bd7398ac9af558b its authentication key. You will also need to specify the certificate and the key for turn.example.org, as well as the SSL connection parameters:
# TURN listener port for TLS (Default: 5349). # Note: actually, "plain" TCP & UDP sessions can connect to the TLS & DTLS # port(s), too - if allowed by configuration. The TURN server # "automatically" recognizes the type of traffic. Actually, two listening # endpoints (the "plain" one and the "tls" one) are equivalent in terms of # functionality; but we keep both endpoints to satisfy the RFC 5766 specs. # For secure TCP connections, we currently support SSL version 3 and # TLS version 1.0, 1.1 and 1.2. # For secure UDP connections, we support DTLS version 1. # tls-listening-port=443 # If the server is behind NAT, you need to specify the external IP address. # If there is only one external address, specify it like this: external-ip=1.2.3.4 # If you have multiple external addresses, you have to specify which # internal address each corresponds to, like this. The first address is the # external ip, and the second address is the corresponding internal IP. #external-ip=172.17.19.131/10.0.0.11 #external-ip=172.17.18.132/10.0.0.12 # Fingerprints in TURN messages are required for WebRTC fingerprint # The long-term credential mechanism is required for WebRTC lt-cred-mech # Configure coturn to use the "TURN REST API" method for validating time- # limited credentials. BigBlueButton will generate credentials in this # format. Note that the static-auth-secret value specified here must match # the configuration in BigBlueButton's turn-stun-servers.xml # You can generate a new random value by running the command: # openssl rand -hex 16 use-auth-secret static-auth-secret=4b85833c7fdf06130bd7398ac9af558b # If the realm value is unspecified, it defaults to the TURN server hostname. # You probably want to configure it to a domain name that you control to # improve log output. There is no functional impact. realm=example.com # Configure TLS support. # Adjust these paths to match the locations of your certificate files cert=/etc/letsencrypt/live/turn.example.org/fullchain.pem pkey=/etc/letsencrypt/live/turn.example.org/privkey.pem # Limit the allowed ciphers to improve security # Based on https://hynek.me/articles/hardening-your-web-servers-ssl-ciphers/ cipher-list="ECDH+AESGCM:ECDH+CHACHA20:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:RSA+AESGCM:RSA+AES:!aNULL:!MD5:!DSS" # Enable longer DH TLS key to improve security dh2066 # All WebRTC-compatible web browsers support TLS 1.2 or later, so disable # older protocols no-tlsv1 no-tlsv1_1 #no-tlsv1_2
Important
You can use any other port instead. You need port 443, however, to deal with some NAT restrictions.
Launch the TURN server:
/etc/init.d/turnserver start
Now add it to autostart:
rc-update add turnserver